Throughout history incidents of targeted violence and assassination have been prompted by various motives—political gain, personal fame, a grievance, a real or perceived wrong, or jealousy from a fantasy (or real) relationship. Acts of targeted violence are premediated, planned, and predatory. They do not occur by happenstance, in contrast to affective or impulsive violence.1 The process of targeted violence starts long before the act of violence.
The assassinations of Julius Caesar, Archduke Franz Ferdinand, and John F. Kennedy are well-known incidents of targeted violence that changed the course of history. Their attackers’ behaviors prior to the attack were not dissimilar to less famous incidents like the ones involving Hollywood celebrity Rebecca Schaeffer and Texas Judge Julie Kocurek (see sidebar). Those attacks might not have changed history, but Rebecca’s murder inspired new anti-stalking laws in California, and then across the United States.2 It also led to the passing of the Driver’s Privacy Protection Act, prohibiting the release of home addresses.3 Julie’s near assassination led to legal and security changes for Texas judges.4
The names of the hundreds of students killed globally due to school attacks might not be well known, but their deaths changed the lives of their families and communities forever. All of these incidents raised awareness, and some changed laws for the betterment of their respective communities. Most of these planned attacks, however, could have been prevented.
Tragic events like targeted violence shock the psyche, leaving people and communities wondering how they could have missed potential red flags or pre-incident indicators (PINs).5 PINs are detectable warning signs that occur before the act of violence. The media often notes after such tragedies that the person “just snapped.” This is never the case in targeted violence. There are discernible behaviors along the path to intended violence.6 Because these behaviors create a different baseline of actions and statements by the potential attacker, they are observable by family, friends, coworkers, community members, or police. If reported, these observed behavioral changes could trigger prevention and intervention measures to mitigate risk. Unfortunately, many times these PINs are seen but dismissed.
Through the lens of hindsight, police, domestic violence victims, stalking victims, threatened judges, and school administrators or human resource managers dealing with problem behaviors in their environments know these PINs all too well.
Pathway Behaviors
As security specialist Gavin de Becker wrote in The Gift of Fear, “Does an assassination attempt begin when the gun is fired at the victim, or when it is drawn, or when it is carried into the arena, or when it is loaded, or when it is purchased, or when assassination is first thought of?”7
There is an abundance of academic research that supports the path to intended violence process. In Threat Assessment and Management Strategies: Identifying the Howlers and the Hunters, threat management consultants Frederick Calhoun and Stephen Weston describe the pathway as moving through six stages: grievance (motive or reasoning), ideation (justifying the act), research and planning (how the act will be carried out), pre-attack preparation (obtaining the weapon of choice), probing and breaches (initiating the plan), then the attack (the assault).8
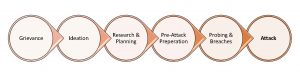
The first three stages offer an indication that something may be afoot. These stages are important and possibly observable (i.e., a first point of intervention), but they do not include illegal actions. These thoughts and plans can occur out of the public eye. Mobilization to action begins at the preparation stage, where the future attacker’s actions may be unprotected by law and where the attacker must take overt actions in furtherance of the plan.
It is at this point that an attacker’s plan becomes vulnerable and, therefore, preventable, and it is also the point where an engaged and educated community, family member, or guardian can “see something, say something.” This simple motto has been effective globally and has had a significant impact in curtailing violence, especially in schools and the workplace. However, in many communities, “seeing” does not equate to “saying” due to a mistrust of police or a fear of being identified as untrustworthy or a snitch. Therefore, community policing initiatives are critical to early identification and prevention.
Community Policing and Threat Assessment
Policing principles were established almost two centuries ago by British statesman Sir Robert Peel. Of the nine principles he developed as a framework for London’s Metropolitan Police Force, the seventh principle, “The police are the public and the public are the police,” is foundational to modern community policing initiatives.9
Community policing is proactive policing and directly related to public safety. With the aim of inspiring confidence in the police through empowerment, it involves partnerships, problem-solving, and trust with public stakeholders. Acts of targeted violence do not occur out of thin air; Peel’s seventh principle can be a driving force in abating this violence. Some individuals who commit predatory violence, such as active shooters, are often the ones hurting or feeling marginalized. Effective communication between the police, community, and mental health professionals can help identify these individuals and offer needed care before something ever happens.
If Peel were alive today, his tenth principle could likely be, “Develop a threat assessment and management program.” It is the next evolutionary step in 21st century policing. Threat assessment and management, a cornerstone to mitigating targeted violence in schools and workplaces, is atypical of traditional policing and a paradigm shift for police today. It requires a new culture of thinking and training.
Enforcing the law and identifying, assessing, and managing a potential threat require different skill sets. Policing investigates a crime that has happened, arrests the perpetrator, and takes evidence to a prosecutor for conviction. Threat assessment and management moves that model to a preventative role, with actions that many times never lead to arrest or conviction. Often, a watch-and-wait strategy is best for the potential offender and requires long-term case monitoring; however, this is but one example of a nuanced protective role. Threat assessment is not punitive (a police action); it is aimed at prevention and intervention (a threat assessment and management role). Duly trained officers can bridge this difference.
 Law enforcement agencies with a dedicated protective mission, such as the U.S. Marshals Service, Ontario Provisional Police, Shin Bet, and various local and national dignitary protection units, subscribe to a protective intelligence strategy that informs the protective mission, and vice versa. These skills would be a vital addition to a police department’s understanding of day-to-day potential community-originated violent behavior. These protective officers are trained specifically to prevent their protectees from harm and understand that making and posing a threat are vastly different and thus require different analysis and response. It is a skill set that fits perfectly into assessing spousal abusers, stalkers, and school or workplace threats too.
Law enforcement agencies with a dedicated protective mission, such as the U.S. Marshals Service, Ontario Provisional Police, Shin Bet, and various local and national dignitary protection units, subscribe to a protective intelligence strategy that informs the protective mission, and vice versa. These skills would be a vital addition to a police department’s understanding of day-to-day potential community-originated violent behavior. These protective officers are trained specifically to prevent their protectees from harm and understand that making and posing a threat are vastly different and thus require different analysis and response. It is a skill set that fits perfectly into assessing spousal abusers, stalkers, and school or workplace threats too.
Inhibitors and Triggers
Targeted attacks can be triggered by one or many events in a person’s life. There are several milestones that someone on the pathway to violence may go through that help spark homicidal thinking and behaviors. Inhibitors are positive influences that can diminish the chance of attack, and triggers are catalysts—a last straw—that prompts violence. Both can come from family and home, religion or ideology, finances, workplace, community, and health and wellness.
Knowing what questions to ask requires the investigator or assessor to explore the various factors associated with high risk and to consider answers that will improve their understanding. This information also helps enhance a protective strategy for the subject and community.
While too many to list in full here, additional factors to consider in an assessment include recent weapons purchases and presence of a weapons persona, knowledge of the target, a police record (and what are the calls for service based on), suicidality, anniversary dates, residency, and hospitalization, to name a few. No matter how far along the pathway to violence, inhibitors can halt further action.
The actions of someone contemplating violence can best be described in four elements: justification, alternatives, consequences, and ability (JACA).10 From the attackers’ perspective, their violence may feel justified, they see no other alternative, they are willing to accept the consequences, and they have the ability to commit the attack. Skilled law enforcement and threat assessors know to look for inhibitors and triggers when conducting a threat assessment and use that information accordingly.
Protecting Our Kids
There is no single profile of a school shooter, nor one of any assassin for that matter, and why it is so important to assess behavior, not just words.11 School shooting massacres have become all too common, with most threat actors being victims of bullying, having prior contact with law enforcement, and school disciplinary problems, according to a recent U.S. Secret Service study.12 Although, it is important to acknowledge that some other killers were well-liked, had good grades, and had no disciplinary issues. A common trigger with all was they wanted to punish those they felt were responsible for their suffering (real or perceived), known as externalization of blame.13 JACA explains well their commitment to action.
Threat assessments are essentially a diagnosis of the behavior and a snapshot in time. The next step is treatment—counseling, independent study, discipline, arrest, etc. Assessment falls into three triage buckets: (1) Is the threat or behavior likely to require no action? (2) Does it require further action? (3) Does it require immediate action?14
Often, employers and school administrators use removal as the means to an end. “Out of sight out of mind” can be an unfortunate treatment plan as the ability to monitor is lost, creating challenges for threat assessors. It is understandable that this may be the only option, but it is imperative that someone removed (or fired) and, therefore considered to be high risk, is handled appropriately and afforded all opportunities to “land softly” with dignity intact.
During this entire process, it is incumbent that the person’s safety net be developed and reinforced. This goes beyond the immediate target, too, as managing victim fear, which includes other students and staff, will be paramount to the school’s overall well-being (and recovery if an incident happens).
Conclusion
The challenges facing law enforcement executives today are numerous. Communities require consistent leadership and transparency in a changing world. Leveraging resources, working with community stakeholders, and training officers on threat assessment and management strategies will enhance safety and security for all. d
Notes:
1 J. Reid Meloy and Jens Hoffman, International Handbook of Threat Assessment (New York, NY: Oxford University Press, 2014).
2 California Penal Code §646.9.
3 Driver’s Privacy Protection Act of 1993, 18 U.S.C. §2721.
4 Judge Julie Kocurek Judicial and Courthouse Security Act of 2017, Texas S.B. 42.
5 Gavin de Becker, The Gift of Fear: Survival Signals that Protect Us from Violence (New York, NY: Dell Publishing, 1997).
6 Robert A. Fein and Bryan Vossekuil, Protective Intelligence Threat Assessment Investigations: A Guide for State and Local Law Enforcement Officials (Washington, DC: National Institute of Justice, 2000).
7 De Becker, The Gift of Fear, 119–120.
8 Frederick S. Calhoun and Stephen W. Weston, Threat Assessment and Management Strategies: Identifying the Howlers and Hunters (Boca Raton, FL: CRC Press, 2008).
9 “Sir Robert Peel’s Nine Principles,” New Westminster Police.
10 De Becker, The Gift of Fear.
11 Fein and Vossekuil, Protective Intelligence Threat Assessment Investigations.
12 U.S. Secret Service National Threat Assessment Center, Protecting America’s Schools: A U.S. Secret Service Analysis of Targeted School Violence (Washington, DC: U.S. Department of Homeland Security, 2019.)
13 Kris Mohandie, “Threat Assessment in Schools” in International Handbook of Threat Assessment.
14 Gavin de Becker & Associates, “Advanced Threat Assessment Academy.”
Please cite as
John F. Muffler, “Mitigating Targeted Violence in Our Communities: Learned Lessons from Past Attacks,” Police Chief Online, June 3, 2020.



