Dropping bombs, capturing for interrogation without warrant, intentionally causing infighting to cause groups to fall apart—all are acceptable in times of war. However, all are unacceptable tactics for a police agency to mitigate gang problems. Despite this very important difference, there are tactics and software developed by the military that have law enforcement applications. Once such tool, Social Network Analysis (SNA), is used by the military to identify terrorist groups and to identify the structure of these groups. Once the structure is identified, strategic planning and action can take place for group disruption.1
One of the best uses of SNA for law enforcement would be to identify gang members and a gang structure, followed by legal and publicly palatable police actions. The desired outcome would be to eradicate a significant amount of violent crime associated with strong gangs, and perhaps transform some gang members by changing their life path in a positive direction. However, challenges exist that agencies must successfully address for a successful implementation of an SNA program.2
What Is Social Network Analysis?
SNA is a method for identifying individuals and groups in a network of people and presenting the data in a visual manner that is quick and easy for minimally trained personnel to understand. The visualization is referred to as a sociogram.3 A sociogram is an easy to understand visualization built from complex computations based on graph theory, a quantitative and analytical methodology used to display complex relationships. The visualization is based on people and relationships, demonstrated by nodes and lines. The nodes denote people, and the lines denote relationships. Social connectivity, prominence, and social roles are clearly displayed in an intuitive format, as seen in Figure 1. This visualization is important because when addressing a nefarious group, such as a gang, knowing the structure defines the approach to be taken by the police.4
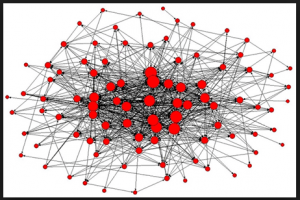
For instance, a long-standing gang with multiple generations of members would look like a bound group with many common ties. A newer gang may be made of smaller groups getting together to form a larger group; thus, it would have fractured groups with a low amount of cohesiveness and communication. In an established gang, removing one or two key people would not necessarily have the desired effect of disrupting the group. However, infiltrating the group with an informant or developing an informant who is already established in the gang could be very productive in a disruption campaign by law enforcement. On the other hand, in a fractured group with key communicators, an informant might not be productive, while identifying and targeting key individuals for surveillance and arrest could prove to be a very effective strategy. Understanding the network allows law enforcement to select the approach most likely to succeed.
SNA Background and Law Enforcement Pilot Project
Military planners realized this approach could be productive when dealing with terrorist groups as early as 1975. Software capability and tactics went into full development after the September 11, 2001, attacks on the World Trade Center. The software and tactics development created the ability to identify and respond to terrorist groups effectively. Federal government personnel speculated that the software and identification methods could apply to law enforcement for gang and organized crime disruption after the success seen by the military.5
The Naval Postgraduate School (NPS) in Monterey, California, is home to the Common Operational Research Environment (CORE) Lab that leads a project to work with law enforcement partners to incorporate SNA methods into crime reduction strategies. Technical how-to is provided, but the response model and adaptation to law enforcement agencies require further development. This development phase is where the shortcomings can become apparent and where planners must expend their effort for any subsequent program to be effective.6
Establishing and Defining Data for SNA
For SNA to work, a data set must be created and, to establish a data set, the correct data must first be established and defined. This sounds simplistic—name, general identifying information, friends, and relatives. However, when one takes a closer look at data bank extraction and the number of potential sources of data, problems begin to surface. One source may list an address as “123 Olive Street,” while the next may list it as “123 Olive St.” To complicate matters further, if two brothers in a gang live at the same address, but the information comes from two sources and is formatted differently, data then becomes incompatible and might not be recognized as the same location by SNA software.7 In fact, the various sources of data are virtually as unlimited as an analyst’s imagination.
Arrest information, jail information, emergency contact information, data gained from cellular telephones, social media—the sources of data are nearly limitless. It is common in U.S. law enforcement field interview cards to have input areas for designated information. The structure of the cards will often need to be adjusted to allow further data such as associates and family members who are with the subject of the field interview to allow for an expansion of the data based on field contacts and to increase the effectiveness of SNA.8 Getting all of the sources of information and the data to assimilate into an Excel document for input into ORA (a network analysis tool) must occur for the data processing. Once data purity is established and input is successful, the ORA software utilizes filters to display the data.9 Unfortunately, the data management job does not end here. Information changes, expires, and requires verification; the best and most up-to-date information often comes from field officers, so proper training and diligent actions by street officers are necessary for timely data collection.10
SNA software allows the analyst to use filters to meet the needs of the analyst and strategic planners. Sociograms can display parameters such as centrality. Once the filters are in place, the structure of the group is defined, and the key people are identified based on the filtration, a strategic plan can then be created.11 This is where the diversion from military tactics takes place, and the uncharted territory for law enforcement begins.
Solution: Using a Targeted Sociogram to Disrupt Gangs
Upon establishing a sociogram how does law enforcement proceed? Proper analysis of the structure should be quick and easy at this point. Is the sociogram tight-knit and structured, or is it fractured and spread out? These questions, when answered, are the very basis for strategic planning. Planned responses may include informants, targeted surveillance and arrest, or contacting the key individuals and informing them of the findings to dissuade criminal behavior. Further alternatives could be the implementation of anti-violence programs, such as those designed to curb firearms violence through social outreach.
The implications of SNA for the future of law enforcement and gang disruption are significant.12 Multiple software platforms are coming forward to facilitate SNA, such as Gephi and XANALYS, along with well-established software, such as Pajek.13 Though NPS support certainly accelerates the learning curve, agencies wishing to utilize SNA who will not garner support due to size or crime statistics will still be able to find affordable software or can explore partnering with an NPS-sponsored pilot agency.
In the future, as artificial intelligence (AI) becomes more prominent, data collection and preparation will become faster and more thorough. Other potential enhancements include facial recognition software that can automatically identify people acting in association with one another.14 Eventually, the data could be input directly into ORA or perhaps more advanced software, and basic strategic planning can occur before human review even occurs. SNA is a smart tool for the recognition of future threats and opportunities to overcome nefarious activities.
Conclusion
With the threat of gang activity, law enforcement must stay ahead technologically. Gangs are using the Internet, smartphones, and computers to communicate and to avoid detection. The digital footprints left behind can be exploited by law enforcement to identify networks involved in criminal activity. When coupled with street contacts and a wide array of creative data seeking, clear pictures for strategic planning emerge. As departments come online with SNA, and adjacent cities share data, law enforcement will see this new phase in the opportunity to disrupt gang activity come to fruition. With the steep learning curve, the time for agencies to act is now in order to prevent gangs from moving to a technological position of advantage. The tools are available now, and the future of SNA looks to be even more effective when AI becomes a viable option for data collection and manipulation.
Notes:
1 David Cunningham, Sean Everton, and Philip Murphy, Understanding Dark Networks: A Strategic Framework for the Use of Social Network Analysis (Lanham, MD: Rowman & Littlefield Publishers, 2016).
2 Giulia Berlusconi et al., “Link Prediction in Criminal Networks: A Tool for Criminal Intelligence Analysis,” PLoS ONE 11, no. 4 (April 2016).
3 Cunningham, Everton, and Murphy, Understanding Dark Networks.
4 Stanley Wasserman and Katherine Faust, Social Network Analysis: Methods and Applications (New York, NY: Cambridge University Press, 2016).
5 Cunningham, Everton, and Murphy, Understanding Dark Networks.
6 Kenneth A. Stewart, “CORE Lab Helps Law Enforcement Explore Social Network Analysis,” Naval Postgraduate School, 2016.
7 Cunningham, Everton, and Murphy, Understanding Dark Networks.
8 Michael Aspland, (faculty associate, Naval Postgraduate School, CORE Lab) personal communication, 2016.
9 Kathleen M. Carley, ORA Quick Start Guide (Pittsburgh, PA: Carnegie Mellon University, Netanomics, 2016).
10 Wasserman and Faust, Social Network Analysis.
11 Seifedine Kadry and Mohammed Z. Al-Taie, Social Network Analysis: An Introduction with an Extensive Implementation to a Large-scale Online Network Using Pajek (Bentham eBooks, 2014).
12 Kadry and Al-Taie, Social Network Analysis.
13 Devendra Desale, “Top 30 Social Network Analysis Visualization Tools,” KDnuggets, June 2015.
14 Agusti Solanas and Antoni Martínez-Ballesté, eds., Advances in Artificial Intelligence for Privacy Protection and Security, Intelligent Information Systems, vol. 1, (Hackensack, NJ: World Scientific Publishing Co. Pte. Ltd., 2009).



