Chiefs, sheriffs, or other law enforcement executives responsible for an agency’s access to the FBI Criminal Justice Information Services (CJIS) Division’s systems and information and control of related criminal justice information (CJI), was probably not thinking on September 30, 2024, “I really wish our next CJIS audit was sooner.” How many U.S. police leaders are intimately familiar with their agency’s last FBI or state audit results and subsequent corrective action plan and attainment? Do they understand exactly where CJI is within the enterprise and how it propagates? Within the complex patchwork of modern law enforcement agency technology, are the technology providers and vendors that have access to the agency’s CJI fully aware of how and where CJI is being processed, networks across which it transits, and systems where it is stored? What about understanding the real differences between on-premises technology, software as a service, platform as a service, or infrastructure as a service solutions that have a relationship to their CJI and the degree of actual control and safeguarding they each provide? Finally, how many executives fully understand the challenges that confront their agency’s CJIS team—and where they are succeeding and where they need help? These are weighty if not uncomfortable technical questions which in many agencies are managed at levels well below the chief executive. These are also the underlying reasons that CJIS Security Policy exists.
What Is Meant by “Modernizing” the CJIS Security Policy?
The FBI’s CJIS Security Policy is undergoing a significant modernization effort to align its security controls with those outlined in the National Institute of Standards and Technology (NIST) Special Publication 800-53 at the moderate level and bears on which security controls were selected for inclusion. This alignment is crucial for enhancing the protection of CJI and ensuring consistency with U.S. federal information security standards.1
Why Is Modernization Necessary?
The primary reason for modernizing the CJIS Security Policy to mirror NIST 800-53 controls is to enhance the overall security posture of criminal justice agencies. NIST 800-53 provides a comprehensive set of security controls that are widely recognized and adopted across various federal agencies. By aligning with these moderate-level controls, the CJIS Security Policy can ensure that criminal justice agencies are implementing robust and standardized security measures. This alignment also facilitates better interoperability and data sharing between federal and state agencies, which are essential for effective law enforcement operations.2
What Challenges May Exist for Law Enforcement Agencies?
Modernizing the CJIS Security Policy presents several challenges for law enforcement agencies and other users of CJI. Many agencies may experience resource constraints, especially smaller ones. These organizations may lack the necessary financial and human resources to rapidly implement the new security controls effectively, especially given their unique technological and organizational context such as existing solutions, contracts, budgets, and operational impacts.
Further, ensuring that all personnel are adequately aware of specific changes and appropriately trained on the new security requirements is a significant undertaking especially given competing demands upon available training time. This includes not only agency IT staff but also officers and administrative personnel who access and handle CJI.
Technical integration of these numerous new security controls into existing systems can result in technical complexity and may require significant upgrades or replacements of legacy systems, which are incapable of compliance.
“These audits focus on verifying the implementation and effectiveness of security controls, identifying vulnerabilities, and ensuring that CJI is adequately protected.”
That gives way to a broader set of CJIS Security compliance and audit considerations than what currently exist.3 Agencies must ensure that local policy is updated to reflect modernization changes and that continuous compliance with the updated policy occurs, which may involve more rigorous and frequent self-assessment to prepare for state and FBI audits.
The CJIS Security Policy Modernization effort will likely have an impact on various state, county, and city information technology organizations as well as commercial partners. While these entities are not law enforcement agencies, they are critical to the technology enterprise and operations of the law enforcement agencies they serve.
State and local information technology organizations are regularly found servicing not only law enforcement agencies but also broader government technology needs. These organizations may need to precisely understand their interaction with CJI and how the CJIS Security Policy change impacts them as they service a law enforcement agency or other organization dealing with CJI. Modernization may require an update of their security frameworks to ensure that all systems handling CJI comply with the new controls. Given these organizations handle both CJIS and other unrelated customers, modernization may involve focused changes to policies, procedures, and technical infrastructure. However, it is law enforcement’s responsibility to share these changes with them and ensure that compliance occurs.
Simultaneously, vendors or commercial partners providing technology solutions to law enforcement agencies will need to ensure their products and services comply with the relevant updated security controls. That said, once again, the law enforcement agency customers are responsible to ensure this compliance exists. This third-party CJIS Security Policy compliance requires attestation, assurance, and assessment throughout the entire life cycle of an agency’s contractual relationship with commercial partners. This may lead to increased costs and development time as vendors work to align their offerings with the new standards.4
What Resources Exist to Help Address These Challenges?
Despite the challenges noted, there are numerous resources available. Some are listed below to help agencies and technology partners navigate the modernization process:
- State CJIS Authorities: The state CJIS representatives highly recommend starting with them first and communicating frequently with state officials. They have detailed resources, tools, and training relevant to state-specific policies and can help agencies achieve compliance. This collaboration is also an opportunity to pool resources at the state level and set priorities for vendors.
- FBI CJIS ISO Program: The FBI’s CJIS Information Security Officer (ISO) Program provides guidance and support to agencies implementing the new security controls. This includes detailed mapping documents that correlate CJIS Security Policy requirements with NIST 800-53 Moderate controls.5
- Training Programs: Various training programs and workshops are available to help agencies understand and implement the new security controls. The IACP created a CJIS Security Policy Modernization Working Group that has analyzed the changes and related impacts and created various training vehicles to assist, such as a podcast series and association conference training sessions.6 These training programs often include practical Q&A and notional case studies to facilitate learning. The IJIS Institute similarly created a CJIS Security Modernization working group that has developed a series of detailed companion guides for each major set of security controls to assist responsible individuals better understand and respond to these changes.7
- Grants and Funding: Federal and state grants may be available to help agencies cover the costs associated with upgrading their security infrastructure. Agencies should explore these funding opportunities to alleviate financial burdens.
- Collaboration and Information Sharing: Agencies can benefit from collaborating with other law enforcement entities and sharing best practices and lessons learned. This can help streamline the implementation process and address common challenges more effectively.
Prioritization of Modernization in CJIS Security Policy v5.9.5
The CJIS Security Policy version 5.9.5 introduces significant updates to align with NIST 800-53 moderate controls, with a clear prioritization framework for implementation and auditing. The policy categorizes security controls into different priority levels, with Priority 1 (P1) controls being the most critical.
Priority 1 Security Control Changes
On October 1, 2024, P1 modernization of CJIS Security Policy took a giant leap forward. P1 controls are considered essential for the protection of CJI and are given the highest implementation and auditing priority. These controls are immediately sanctionable upon publication of the policy, meaning agencies must comply with these requirements without delay. Key aspects and enhancements of P1 controls noted in Table 1 follow:
- Access Control (AC): 7 enhancements
- Configuration Management (CM): 5 enhancements
- Identification and Authentication (IA): 2 enhancements
- Risk Assessment (RA): 1 enhancement
- Systems and Communication Protection (SC): 1 enhancement
- Systems and Information Integrity (SI): 5 enhancements
Table 1 quickly details the P1 enhancements and what changes are auditable right now.8
Table 1: P1 Security Control Changes
| Number | Control Name | Enhancements |
| AC-2 | Policy and Procedures | AC-2 (1)(2)(3)(4)(5)(13) |
| AC-3 | Access Enforcement | AC-3 (14) |
| AC-4 | Information Flow Enforcement | AC-4 |
| AC-5 | Separation of Duties | AC-5 |
| AC-6 | Least Privilege | AC-6 (1)(2)(5)(7)(9)(10) |
| AC-17 | Remote Access | AC-17 (1)(2)(3)(4) |
| AC-20 | Use of External Systems | AC-20 (1)(2) |
| CM-2 | Baseline Configuration | CM-2 (2)(3)(7) |
| CM-5 | Access Restrictions for Change | CM-5 |
| CM-6 | Configuration Settings | CM-6 |
| CM-7 | Least Functionality | CM-7 (1)(2)(5) |
| CM-8 | System Component Inventory | CM-8 (1)(3) |
| IA-2 | Identification and Authentication (Organ. Users) | IA-2 (1)(2)(8)(12) |
| IA-5 | Authenticator Management | IA-5 (1)(2)(6) |
| RA-5 | Vulnerability Monitoring and Scanning | RA-5 (2)(5)(11) |
| SC-7 | Boundary Protection | SC-7 (3)(4)(5)(7)(8)(24) |
| SI-2 | Flaw Remediation | SI-2 (2) |
| SI-3 | Malicious Code Protection | SI-3 |
| SI-4 | System Monitoring | SI-4 (2)(4)(5) |
| SI-7 | Software, Firmware, and Information Integrity | SI-7 (1)(7) |
| SI-10 | Information Input Validation | SI-10 |
Agency CJIS teams should be working with their applicable CJIS teams to facilitate training, implementation, and compliance—it is critical that agencies are communicating with their state CJIS officials in this regard.
What Is the Timeline for Implementing and Auditing These Changes?
The implementation of P1 controls is prioritized to mitigate cybersecurity risk and ensure immediate compliance. These controls are auditable from the date of policy publication, meaning agencies must be prepared for audits and demonstrate compliance with these critical security measures. The focus on P1 controls underscores their importance in safeguarding CJI and maintaining the integrity of criminal justice operations.
The prioritization of P1 security controls in CJIS Security Policy v6.0 reflects the urgency and importance of these measures in protecting CJI. Law enforcement agencies and other users of CJI must prioritize the implementation of these controls to ensure compliance and enhance their overall security posture. While the task is formidable, the structured prioritization helps agencies focus their efforts on the most critical areas first, paving the way for a more secure and resilient CJI system. Existing and P1 controls are fully auditable as of October 1, 2024. P2 through P4 controls will be fully auditable in 2027.9
How Can Agencies Effectively Prepare for an Audit?
Effective preparation requires a collaborative approach. Teamwork establishes relationships and trust between local agencies and the state and between the state and the FBI. Again, agencies should talk to their state CSO/ISO early and discuss audit timelines and preparation.
More broadly, this effectively means developing appropriate partnerships. Figure 1 was developed by IACP CJIS Security Working Group members, to include state CSOs and ISOs, and depicts a Venn diagram that emphasizes development of a proactive pre-audit approach and relationship building between key stakeholders to create critical connections, deepen understanding, inspire reaction and response, and create trust. This is important in the face of change to achieve compliant outcomes.
- Relationship and Awareness establish a critical Connection.
- Relationship and Realistic fosters deeper Understanding.
- Awareness and Realistic motivation a Reaction or inspire a Response.
- Relationship, Awareness, and Realistic combine to create Trust for Collaborative Pro-
Action.
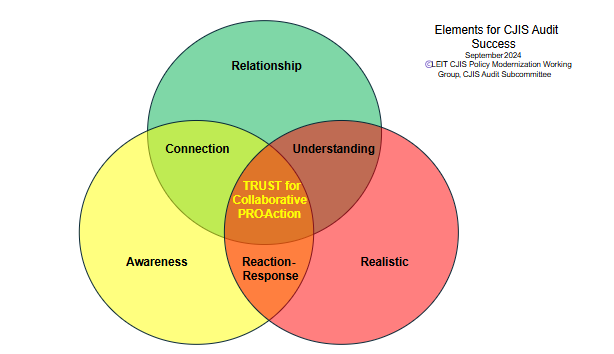
Beyond the audit preparation approach, technical audits under CJIS Security Policy Modernization are complex and have become a critical component in ensuring compliance, especially for P1 security controls. Technical audits are comprehensive evaluations of an agency’s information systems, processes, and controls to ensure they meet the security requirements outlined in the CJIS Security Policy. These audits focus on verifying the implementation and effectiveness of security controls, identifying vulnerabilities, and ensuring that CJI is adequately protected.
To prepare for technical audits, agencies should consider the following steps:
- Conduct a Self-Assessment: Perform an internal review of current security controls and practices to identify gaps and areas needing improvement. Use the CJIS Security Policy and NIST 800-53 as benchmarks.
- Review and Update Policies: Ensure that all security policies and procedures are up-to-date and align with the latest CJIS Security Policy requirements. This includes documenting all processes related to access control, incident response, and configuration management.
- Review Technical Controls: Assess whether required technical security controls such as cybersecurity technology and use of encryption align adequately with all efforts to protect CJI. Ensure these controls are properly configured and regularly updated.
- Train Personnel: Provide comprehensive training to all staff on the updated security policies and procedures. This includes IT staff, officers, and administrative personnel who handle CJI.
- Maintain Documentation: Keep detailed records of all security measures, configurations, and changes. This documentation will be crucial during the audit process to demonstrate compliance.
- Regularly Review and Test Controls: Conduct regular reviews and tests of security controls to ensure they are functioning as intended. This includes periodic vulnerability assessments and penetration testing.
- Engage with Vendors: Work closely with technology vendors to ensure their products and services comply with the updated security requirements. This may involve obtaining compliance certifications or conducting joint security assessments.
Preparing for audits under the modernized CJIS Security Policy requires a proactive and comprehensive approach. By focusing on security controls and following the steps outlined, agencies can ensure they are well prepared for audits and can effectively protect CJI. While the process may be challenging, the enhanced security will ultimately benefit the entire U.S. criminal justice system.10
Conclusion
Modernizing the CJIS Security Policy to align with NIST 800-53 is a formidable but necessary task. It enhances the security of CJI, promotes standardization, and facilitates better data sharing across agencies. While the challenges are significant, the available resources and support can help agencies and vendors successfully navigate this transition, ultimately leading to a more secure and efficient criminal justice system.
Notes
1FBI, Criminal Justice Information Service Division (CJIS), Criminal Justice Services (CJIS) Security Policy, Version 6 (2024); FBI, CJIS, Requirements Companion Document to FBI CJIS Security Policy Version 6.0 (2024); FBI, CJIS, Security Control Mapping of CJIS Security Policy Version 5.9 Requirements to NIST Special Publication 800-53 Revision 5 (2021)
2FBI, CJIS, Criminal Justice Services (CJIS) Security Policy, Version 6.
3FBI, CJIS, Requirements Companion Document to FBI CJIS Security Policy Version 6.0.
4FBI, CJIS, Requirements Companion Document to FBI CJIS Security Policy Version 6.0
6IACPlearn, CJIS Security Policy Modernization (podcast series), 2024
7IJIS Institute, “Criminal Justice Information Systems (CJIS) Advisory Committee.”
8FBI, CJIS, Criminal Justice Services (CJIS) Security Policy, Version 6
9FBI, CJIS, Criminal Justice Services (CJIS) Security Policy, Version 6.
10FBI, CJIS, Criminal Justice Services (CJIS) Security Policy, Version 6; FBI, CJIS, Requirements Companion Document to FBI CJIS Security Policy Version 6.0; FBI, CJIS, Security Control Mapping of CJIS Security Policy Version 5.9 Requirements to NIST Special Publication 800-53 Revision 5.
Please cite as
IACP CJIS Security Modernization Working Group, “CJIS Security Policy Modernization: What Police Leaders Should Know,” Police Chief Online, April 23, 2025.



